WordPress is all over the web; it’s the most popular and most used content management system (CMS) out there. Is your website or blog is powered by WordPress? Did you know that malicious hackers are always attacking WordPress sites every minute? If you didn’t, now you know.
The first step towards securing your website or blog is to perform a vulnerability assessment. This is simply an operation to identify common security loopholes (known to the public), within your site or its underlying architecture.
How to Install WPScan in Linux Systems
The recommended way of installing and running WPScan is to use the official Docker image, this will help you do away with installation problems (typically dependency issues).
You should have Docker installed and running on your system, otherwise start by installing it using the following, which will use the cURL program to download and run a shell script that will add the Docker repository to your system and install the needed packages.
$ sudo curl -fsSL https://get.docker.com | sh
Once the Docker is successfully installed, start the service, enable it to auto-start at system boot time and check if it’s up and running as follows.
# sudo systemctl start docker # sudo systemctl enable docker # sudo systemctl status docker
Next, pull the WPScan Docker image using the following command.
$ docker pull wpscanteam/wpscan
Once WPScan Docker image downloaded, you can list the Docker images on your system using following command.
$ docker images
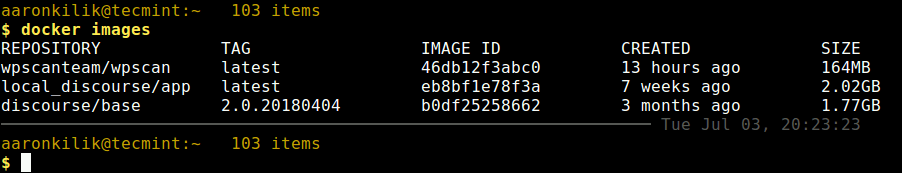
Looking at the output from the following screesnhot, the WPScan repository image is wpscanteam/wpscan which you will use in the next section.
How to Perform WordPress Vulnerability Scan Using WPScan
The simplest way of performing a vulnerability scan using WPScan is to provide your WordPress website’s URL as shown (replace www.example.com with your site’s URL).
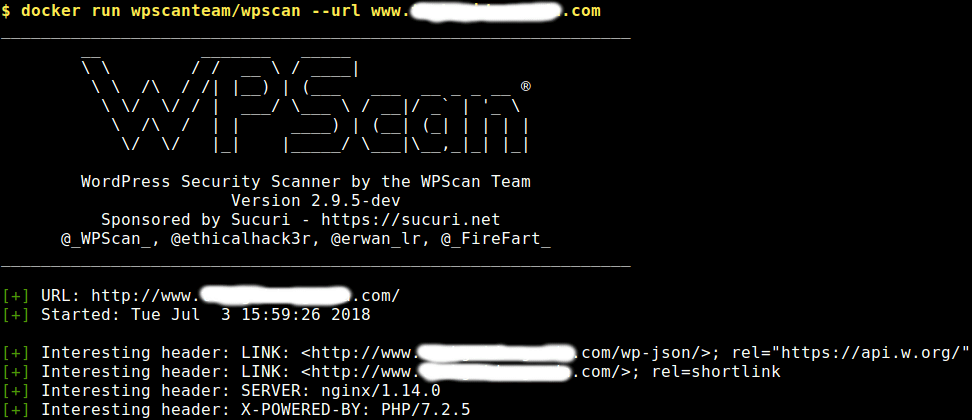
$ docker run wpscanteam/wpscan --url www.example.com
WPScan will try to find interesting HTTP headers such as SERVER (web server type and version) and X-POWERED-BY (PHP version); it will also look for any exposed APIs, RSS feed link and users.
Then it will go on to enumerate the WordPress version and checks if it is up to date or if there are any vulnerabilities associated with the detected version number. In addition, it will try to detect the theme as well as installed plugins to find it they are up to date.
You can perform a wordlist password brute force on enumerated users using 30 threads using the followin command. The --wordlist and --threads flags to specify the wordlist and set the number of threads receptively.
$ docker run wpscanteam/wpscan --url www.example.com --wordlist wordlist_file.txt --threads 30
To carry out a wordlist password brute force on the “admin” username only, run the following command.
$ docker run wpscanteam/wpscan --url www.example.com --wordlist wordlist_file.txt --username admin
Alternatively, you can mount a local wordlist on your system to the docker container and start a bruteforce attack for user admin.
$ docker run -it --rm -v ~/wordlists:/wordlists wpscanteam/wpscan --url www.example.com --wordlist /wordlists/wordlist_file.txt --username admin
To enumerate installed plugins, run the following command.
$ docker run wpscanteam/wpscan --url www.example.com --enumerate p
If enumerating installed plugins is not be enough, you can run all enumeration tools as shown.
$ docker run wpscanteam/wpscan --url www.example.com --enumerate
To enable output debugging, use the --debug-ouput flag, and redirect the output into a file for later analysis.
$ docker run wpscanteam/wpscan --url www.example.com --debug-output 2>debug.log
Last but not least, you can update WPScan’s database to the latest version by executing the following command.
$ docker run wpscanteam/wpscan --update
You can view the Docker and WPScan help messages with these commands.
$ docker -h $ docker run wpscanteam/wpscan -h
WPScan Github repository: https://github.com/wpscanteam/wpscan
That’s all for now! WPScan is a powerful black box WordPress vulnerability scanner that you should have in your arsenal of web security tools.
