Azure Load Balancer vs Application Gateway in Azure
Azure Load Balancer works with traffic at Layer 4, while Application Gateway works with Layer 7 traffic, and specifically with HTTP (including HTTPS and WebSockets).
Azure Application Gateway
Application Gateway (AGW) is a web traffic manager for your web applications (one or multiple) i.e. load balancer that enables you to manage traffic to your web applications.

- With AGW, on top of load balancing your workloads, you can make routing decisions based on URI path or host headers. For example, you can route traffic based on the incoming URL. If /images are in the inbound URL, you can route traffic to a specific set of servers (or pool) configured for images. If /video is in the URL, that traffic is routed to another pool.
2. It can be used to do TLS/SSL termination. TLS/SSL termination can be useful to allow unencrypted traffic between AGW and backend servers saving some of processing load needed to encrypt and decrypt said traffic. However, sometimes unencrypted communication to the servers is not acceptable because of security requirements, compliance requirements, or application may only accept a secure connection. In these situations, Application Gateway also supports end-to-end TLS/SSL encryption.
3. It includes a web application firewall called Web application firewall (WAF) that protects your workload from common exploits like SQL injection attacks or cross-site scripting attacks, to name a few.
4. It provides application delivery controller (ADC) as a service, offering various Layer 7 load-balancing capabilities. Use it to optimize web farm productivity by offloading CPU-intensive SSL termination to the gateway.
Azure Load Balancer
Load balancing refers to evenly distributing load (incoming network traffic) across a group of backend resources or servers. Azure Load Balancer distributes inbound flows that arrive at the load balancer’s front end to backend pool instances. These flows are according to configured load balancing rules and health probes. The backend pool instances can be Azure Virtual Machines or instances in a virtual machine scale set.
It can also provide outbound connections for virtual machines inside your virtual network by translating their private IP addresses to public IP addresses.
It is a TCP/UDP load balancing and port forwarding engine only. It does not terminate, respond, or otherwise interact with the traffic. It simply routes traffic based on source IP address and port, to a destination IP address and port.
Azure Load Balancer is a high-performance, low-latency Layer 4 load-balancing service (inbound and outbound) for all UDP and TCP protocols. It is built to handle millions of requests per second while ensuring your solution is highly available. It is zone-redundant, ensuring high availability across Availability Zones.
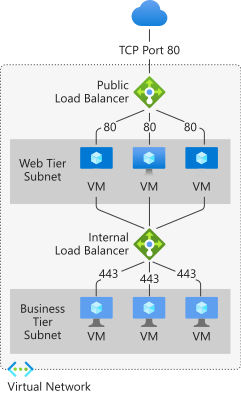
A public load balancer can provide outbound connections for virtual machines (VMs) inside your virtual network. These connections are accomplished by translating their private IP addresses to public IP addresses. Public Load Balancers are used to load balance internet traffic to your VMs.
An internal (or private) load balancer is used where private IPs are needed at the frontend only. Internal load balancers are used to load balance traffic inside a virtual network. A load balancer frontend can be accessed from an on-premises network in a hybrid scenario.
